💜Thank you for correcting me.
I edited it now 😄
I actually wanted to keep the title short, but I think it would be better to edit the title to avoid any confusion to make it clear that it's manufactured in China, rather than saying it in the current way.
Edit: I edited the title to reflect the details better.
Large Language Models (LLMs) have demonstrated remarkable performance in solving complex reasoning tasks through mechanisms like Chain-of-Thought (CoT) prompting, which emphasizes verbose, step-by-step reasoning. However, humans typically employ a more efficient strategy: drafting concise intermedia...

> Large Language Models (LLMs) have demonstrated remarkable performance in solving complex reasoning tasks through mechanisms like Chain-of-Thought (CoT) prompting, which emphasizes verbose, step-by-step reasoning. However, humans typically employ a more efficient strategy: drafting concise intermediate thoughts that capture only essential information. In this work, we propose Chain of Draft (CoD), a novel paradigm inspired by human cognitive processes, where LLMs generate minimalistic yet informative intermediate reasoning outputs while solving tasks. By reducing verbosity and focusing on critical insights, CoD matches or surpasses CoT in accuracy while using as little as only 7.6% of the tokens, significantly reducing cost and latency across various reasoning tasks.
St. Paul’s Lutheran church in Helsinki has held the first church service in Finland created mostly by artificial intelligence.

> A tale of good versus evil played out on the large screen in the sanctuary of St. Paul’s Lutheran church in Finland. Jesus was shown in robes with long hair and a beard, while Satan was dressed in more modern clothes but with a menacing frown and higher-pitched voice — all created by artificial intelligence.
St. Paul’s Lutheran church in Helsinki has held the first church service in Finland created mostly by artificial intelligence.

> A tale of good versus evil played out on the large screen in the sanctuary of St. Paul’s Lutheran church in Finland. Jesus was shown in robes with long hair and a beard, while Satan was dressed in more modern clothes but with a menacing frown and higher-pitched voice — all created by artificial intelligence.
Tarlogic presents research revealing undocumented commands in the ESP32 microchip, present in millions of smart devices with Bluetooth
Source Link Privacy.
https://themarkup.org/blacklight?url=https%3A%2F%2Fwww.tarlogic.com%2Fnews%2Fbackdoor-esp32-chip-infect-ot-devices%2F&device=mobile&location=us-ca&force=false
> Tarlogic Security has detected a backdoor in the ESP32, a microcontroller that enables WiFi and Bluetooth connection and is present in millions of mass-market IoT devices. Exploitation of this backdoor would allow hostile actors to conduct impersonation attacks and permanently infect sensitive devices such as mobile phones, computers, smart locks or medical equipment by bypassing code audit controls.
Tarlogic presents research revealing undocumented commands in the ESP32 microchip, present in millions of smart devices with Bluetooth

Source Link Privacy.
https://themarkup.org/blacklight?url=https%3A%2F%2Fwww.tarlogic.com%2Fnews%2Fbackdoor-esp32-chip-infect-ot-devices%2F&device=mobile&location=us-ca&force=false
> Tarlogic Security has detected a backdoor in the ESP32, a microcontroller that enables WiFi and Bluetooth connection and is present in millions of mass-market IoT devices. Exploitation of this backdoor would allow hostile actors to conduct impersonation attacks and permanently infect sensitive devices such as mobile phones, computers, smart locks or medical equipment by bypassing code audit controls.
Tarlogic presents research revealing undocumented commands in the ESP32 microchip, present in millions of smart devices with Bluetooth

Source Link Privacy.
https://themarkup.org/blacklight?url=https%3A%2F%2Fwww.tarlogic.com%2Fnews%2Fbackdoor-esp32-chip-infect-ot-devices%2F&device=mobile&location=us-ca&force=false
> Tarlogic Security has detected a backdoor in the ESP32, a microcontroller that enables WiFi and Bluetooth connection and is present in millions of mass-market IoT devices. Exploitation of this backdoor would allow hostile actors to conduct impersonation attacks and permanently infect sensitive devices such as mobile phones, computers, smart locks or medical equipment by bypassing code audit controls.
Relevant post about The Guardian privacy.
A better link to keep your privacy, if you want to read the article: https://www.skinnyguardian.xyz/uk/lifeandstyle2025mar08ai-wingmen-bots-to-write-profiles-and-flirt-on-dating-apps/
> What’s new in this release: > - Clipboard support in the Wayland driver. > - Initial Vulkan video decoder support in WineD3D. > - Bundled Compiler-RT library for ARM builds. > - Header fixes for Winelib C++ support. > - More progress on the Bluetooth driver. > - Various bug fixes.
A worker at a DVD and Blu-ray manufacturing and distribution company used by major movie studios was arrested today in Memphis, Tennessee, for allegedly stealing DVDs and Blu-rays of blockbuster movies from the company and selling them before their official scheduled release dates. A digital copy of...

> According to court documents, Steven R. Hale, 37, of Memphis, worked for a multinational company that, among other things, manufactured and distributed DVDs and Blu-rays of movies. From approximately February 2021 to March 2022, Hale allegedly stole numerous “pre-release” DVDs and Blu-rays, that is, discs being prepared for commercial distribution in the United States and not available for sale to the public. These included DVDs and Blu-rays for such popular films as “F9: The Fast Saga,” “Venom: Let There Be Carnage,” “Godzilla v. Kong,” “Shang-Chi and the Legend of the Ten Rings,” “Dune,” and “Black Widow.” Hale allegedly sold the DVDs and Blu-rays through e-commerce sites. At least one pre-release Blu-ray that Hale allegedly stole and sold, “Spider-Man: No Way Home,” was “ripped” — that is, extracted from the Blu-ray by bypassing the encryption that prevents unauthorized copying — and copied. That digital copy was then illegally made available over the internet more than a month before the Blu-ray’s official scheduled release date. Copies of “Spider-Man: No Way Home” were downloaded tens of millions of times, with an estimated loss to the copyright owner of tens of millions of dollars.
YouTube Video
Click to view this content.
YouTube Video
Click to view this content.
The murders of two people outside an LGBTQ+ bar at first looked like the act of a lone shooter. A ProPublica and FRONTLINE investigation shows they were, in fact, the culmination of a coordinated, international recruiting effort by online extremists.

> - Extremist Influencers: Neo-Nazi influencers on the social media platform Telegram created a network of chats and channels where they stoked racist, antisemitic and homophobic hate. > - Targeted Teen: The influencers, known as the Terrorgram Collective, targeted a teen in Slovakia and groomed him for three years to kill. > - Terrorgram Network: Juraj Krajčík subscribed to at least 49 extremist Telegram chats and channels, many of them nodes in the Terrorgram network, before he killed two people at an LGBTQ+ bar.
The murders of two people outside an LGBTQ+ bar at first looked like the act of a lone shooter. A ProPublica and FRONTLINE investigation shows they were, in fact, the culmination of a coordinated, international recruiting effort by online extremists.

> - Extremist Influencers: Neo-Nazi influencers on the social media platform Telegram created a network of chats and channels where they stoked racist, antisemitic and homophobic hate. > - Targeted Teen: The influencers, known as the Terrorgram Collective, targeted a teen in Slovakia and groomed him for three years to kill. > - Terrorgram Network: Juraj Krajčík subscribed to at least 49 extremist Telegram chats and channels, many of them nodes in the Terrorgram network, before he killed two people at an LGBTQ+ bar.
Manga piracy site Tu Manga Online took just 90 days to transform its most recent domain switch from zero to half a billion visits per month.
> New research on ad-funded piracy centers on manga site Tu Manga Online (TMO). After switching to a new domain 'zonatmo.com' around September last year, it took just 90 days to transform a new start into half a billion visits per month. According to the research, the site's revenue generating scheme is an open secret. Yet, for unknown reasons, nobody tries to stop it.
I just wanted to encourage you to upload your videos to PeerTube.
[Not Serious] 3 numbers more.
I’m old enough to remember when age verification bills were pitched as a way to ‘save the kids from porn’ and shield them from other vague dangers lurking in the digital world (like…“the transgender”). We have long cautioned about the dangers of these laws, and pointed out why they are likely to...

I’m old enough to remember when age verification bills were pitched as a way to ‘save the kids from porn’ and shield them from other vague dangers lurking in the digital world (like…“the transgender”). We have long cautioned about the dangers of these laws, and pointed out why they are likely to...

From their about us page:
The Forward has always been a not-for-profit association and is supported by the contributions of its readers.
There's a secret side of YouTube, just beyond the guiding hand of the algorithm – and it’s nothing like what you know.

> There's a secret side of YouTube, just beyond the guiding hand of the algorithm – and it’s nothing like what you know. The vast majority of YouTube's estimated 14.8 billion videos have almost never been seen. Until now.
Thank you for your words, I added also Wired website.
2 things:
they're actually better than the other news sites you list here.
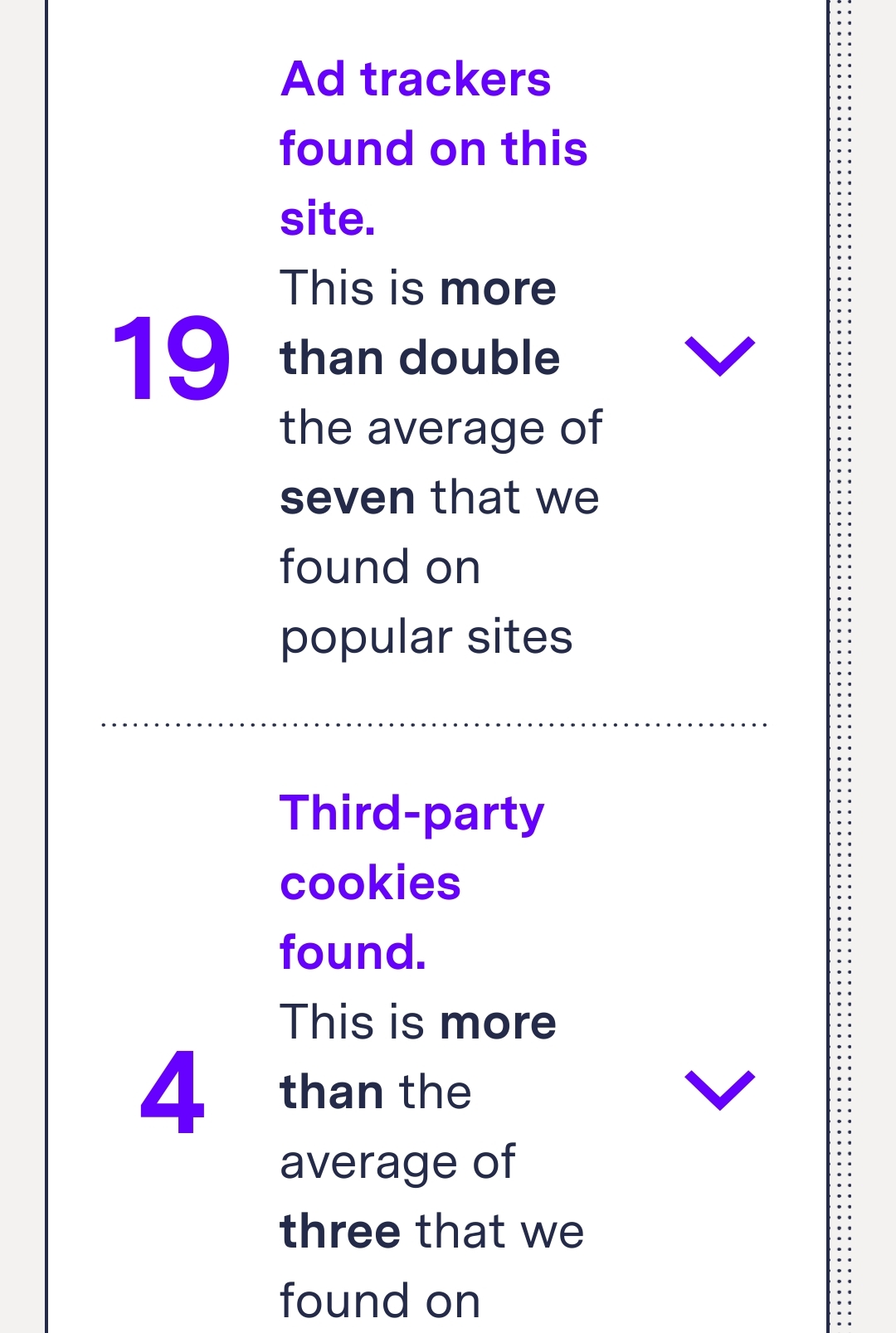
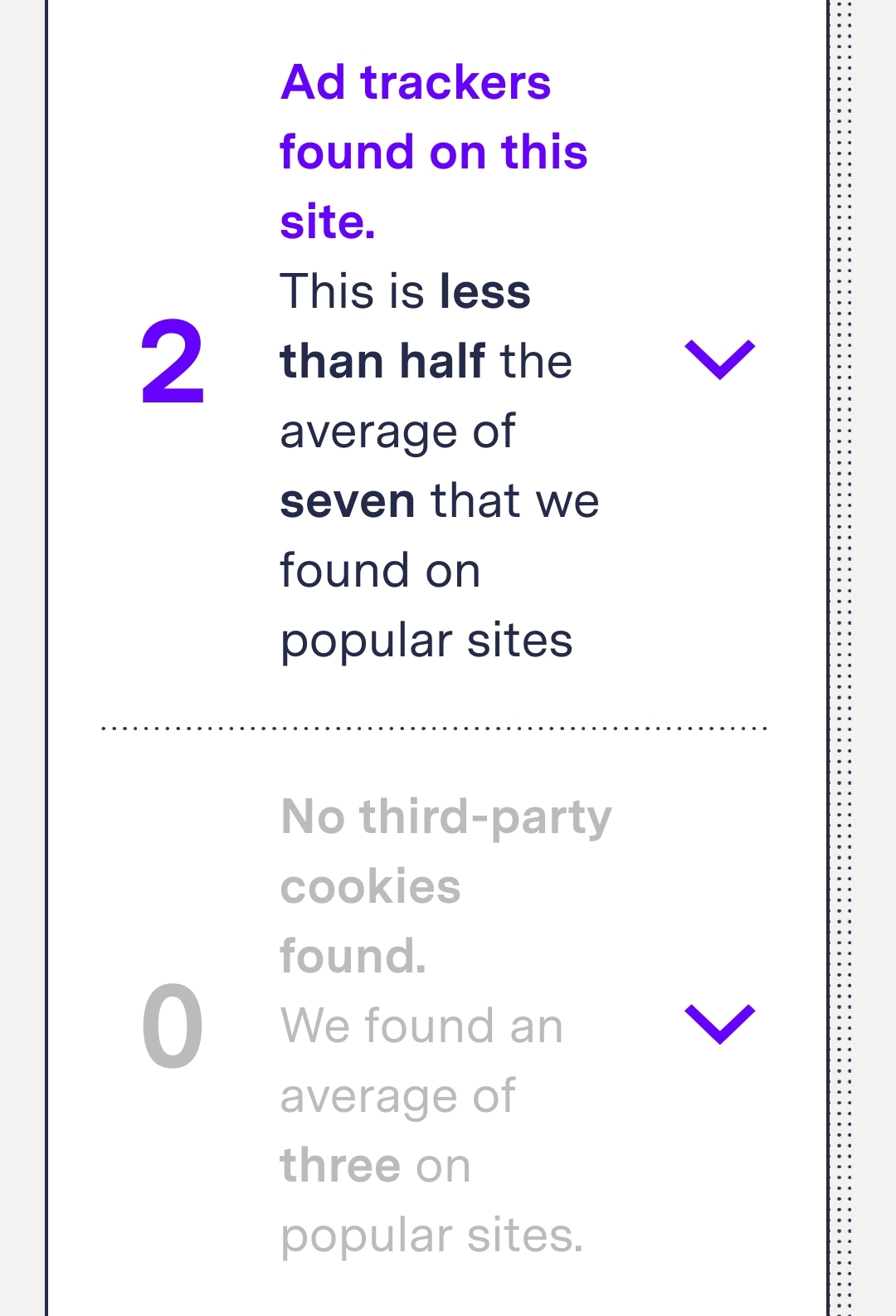
What you are saying does not make any sense unless you did not click the links to see the amount of trackers in the tests.
Either way, I'm using ad-blocking, DNS filtering, and I do general browsing like this in a separate browser that wipes everything on exit sooo 🤷 saves you from worrying about this stuff or even thinking about it much.
Yet you are using Lemmy instead of Reddit? Which means you kind of understand fully that the tools that you are talking about does not protect you 100% , rather they just reduce the amount of trackers tracking you.
Also it's pretty dystopian to support the websites that violates people privacy, instead of using the websites that basically provide the same product with better privacy.
You can read the other websites without JavaScript as well.
Also, that might not stop all the trackers, as the webpages are loaded with their trackers.
If they kept my privacy 100%, sure I could pay up to 3 dollars a month.
If they did not prove themselves to be a better browser in terms of privacy, then what is the purpose of their existence?
I believe the table is correct, maybe the contributor confused them.
Hi,
This is not my project, I just liked it.
You are right, I think it might worth suggesting it to the author on codeberg.
your license
I am not the project leader.
There's too many unknowns
Public domain?
You can do with the project what ever you want with no restrictions.
License?
The person or persons who have associated work with this document (the "Dedicator" or "Certifier") hereby either (a) certifies that, to the best of his knowledge, the work of authorship identified is in the public domain of the country from which the work is published, or (b) hereby dedicates whatever copyright the dedicators holds in the work of authorship identified below (the "Work") to the public domain. A certifier, moreover, dedicates any copyright interest he may have in the associated work, and for these purposes, is described as a "dedicator" below.
A certifier has taken reasonable steps to verify the copyright status of this work. Certifier recognizes that his good faith efforts may not shield him from liability if in fact the work certified is not in the public domain.
Dedicator makes this dedication for the benefit of the public at large and to the detriment of the Dedicator's heirs and successors. Dedicator intends this dedication to be an overt act of relinquishment in perpetuity of all present and future rights under copyright law, whether vested or contingent, in the Work. Dedicator understands that such relinquishment of all rights includes the relinquishment of all rights to enforce (by lawsuit or otherwise) those copyrights in the Work.
Dedicator recognizes that, once placed in the public domain, the Work may be freely reproduced, distributed, transmitted, used, modified, built upon, or otherwise exploited by anyone for any purpose, commercial or non-commercial, and in any way, including by methods that have not yet been invented or conceived.
How do you discover providers on simplex?
No problem, I will resubmit later. I used the wrong article link anyway.