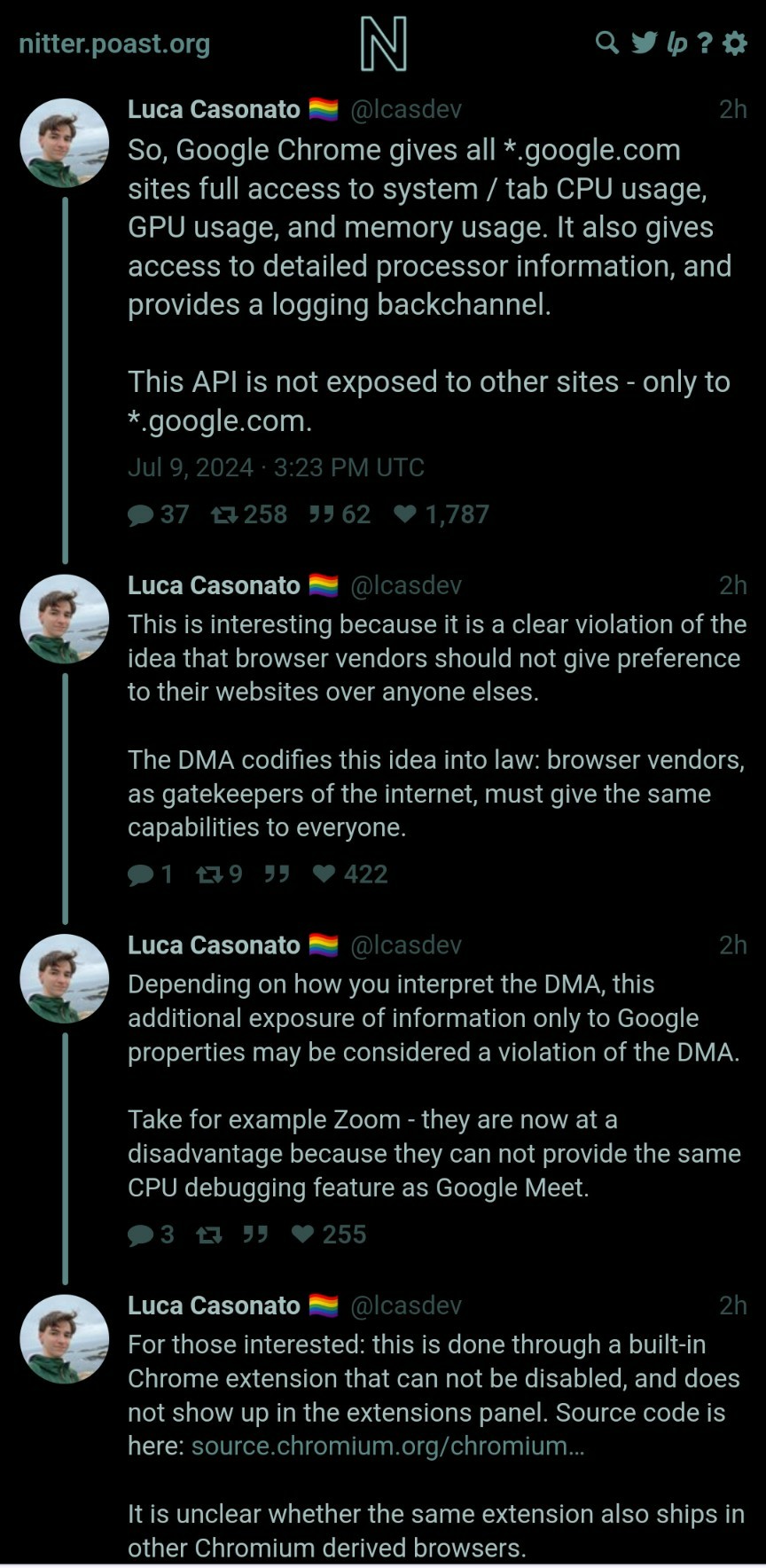
Google Chrome ships a default, hidden extension that allows code on *.google.com access to private APIs, including your current CPU usage
Google Chrome ships a default, hidden extension that allows code on *.google.com access to private APIs, including your current CPU usage

fedi.simonwillison.net
Simon Willison (@simon@simonwillison.net)

cross-posted from: https://lemmy.dbzer0.com/post/23752739
https://simonwillison.net/2024/Jul/9/hangout_servicesthunkjs/
Google Chrome ships a default, hidden extension that allows code on *.google.com access to private APIs, including your current CPU usage