As a researcher I often run into situations in which I need to make a compiled binary do things that it wouldn’t normally do or change the way it works in some way. Of course, if one…

This blog won't dive into any of the mentioned WIFI attacks, but will highlight techniques to retrieve the PSK from a workstation post-compromise instead.

Lass Security's recent research on AI Package Hallucinations extends the attack technique to GPT-3.5-Turbo, GPT-4, Gemini Pro (Bard), and Coral (Cohere).

Advisory ID: usd-2023-0029 | Product: SONIX Technology Webcam | Vulnerability Type: CWE 732 - Incorrect Permission Assignment for Critical Resource

Hides message with invisible Unicode characters. Contribute to dwisiswant0/unch development by creating an account on GitHub.

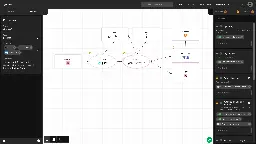
Gram is Klarna's own threat model diagramming tool - klarna-incubator/gram
Anyone who has had to deal with HTML emails on a technical level has probably reached the point where they wanted to quit their job or just set fire to all the mail clients due to their inconsistent implementations. But HTML emails are not just a source of frustration, they can also be a serious sec...

Master Android malware reversal with ease using Incinerator, your trusted ally in the fight against threat actors for experts and novices alike.

I hope you've read the Part-1 of this blog series on basics of AD CS in the environment. In the Part-1 of this blog series, We looked at how we can setup certificate templates or uses the 'User' template to enroll our Windows 7 Minor User with AD CS services. So far we got

DLL Proxy Loading is a technique which an arbitrary DLL exports the same functions as the legitimate DLL and forwards the calls to the legitimate DLL in an attempt to not disrupt the execution flow…
Information Security Services. Offensive Security, Penetration Testing, Mobile and Application, Purple Team, Red Team

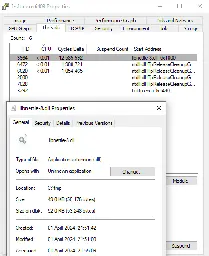
See how Oligo ADR Detects Exploitation of CVE-2024-3094 (XZ backdoor in liblzma).

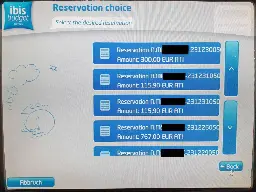
An IBIS hotel check-in terminal leaked room door key codes of almost half of the rooms.
OSINT tool that finds domains, subdomains, directories, endpoints and files for a given seed URL. - caio-ishikawa/netscout

notes, honeypot, and exploit demo for the xz backdoor (CVE-2024-3094) - amlweems/xzbot