
Reverse Engineering
- Introduction to Ghidra: Modding and Reverse Engineering Games
YouTube Video
Click to view this content.
- conduition.io Reverse Engineering TicketMaster's Rotating Barcodes (SafeTix)
"Screenshots won't get you in", but Chrome DevTools will.
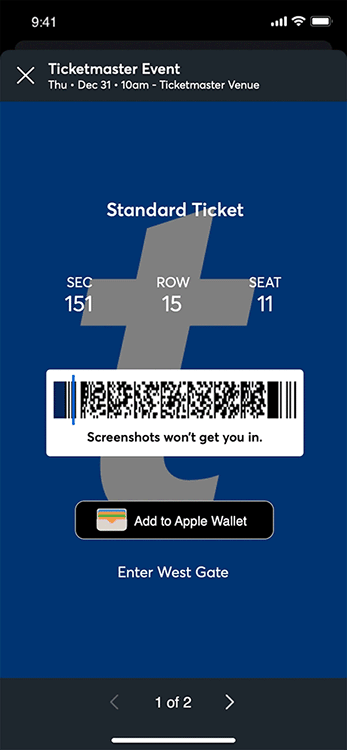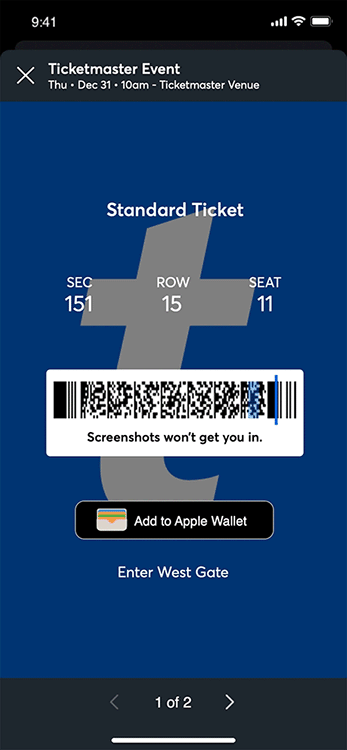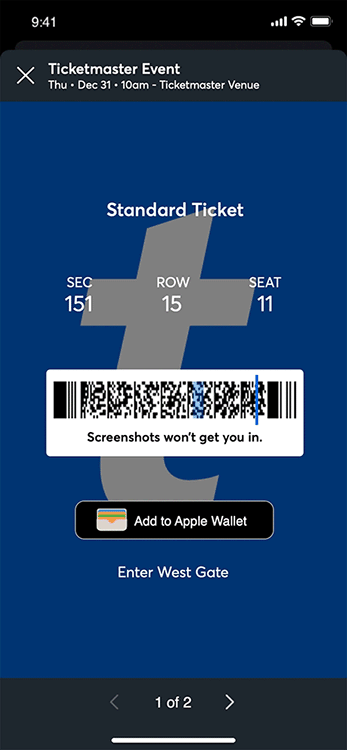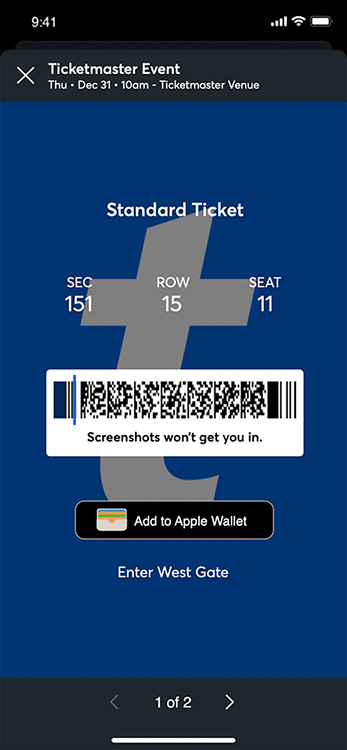
- cookieplmonster.github.io How a 20 year old bug in GTA San Andreas surfaced in Windows 11 24H2
After over two decades, players are now forbidden from flying a seaplane, all thanks to undefined code behavior.

- Adventures of My Oven (Pinocchio) with ChipWhisperercfp.recon.cx Adventures of My Oven (Pinocchio) with ChipWhisperer 2023
You probably wouldn't consider power analysis & fault injection being a required skill set for your oven repair person. But when your oven is actively lying to you and not just broken, a new type of repair is needed beyond just replacing a heating element. This talk starts from a common complaint: h...
- Hacking a Rechargeable Lamp With Non-Standard USB-C Connector
YouTube Video
Click to view this content.
- eshard.com Emulating an iPhone in QEMU
From black screens and boot issues to rendering quirks and PAC puzzles, here’s what we learned getting iOS to finally say hello.

- voidstarsec.com Brushing Up on Hardware Hacking Part 3 - SWD and OpenOCD
In this post we discuss how to commuinicate with an unsupported chip using OpenOCD and review how to write flash programming algorithms in OpenOCD. We also demonstrate how to flash custom firmware to the target device.
- icode4.coffee Hacking the Xbox 360 Hypervisor Part 2: The Bad Update Exploit
Finding and exploiting bugs in the Xbox 360 hypervisor to create the "Bad Update" exploit.

- icode4.coffee Hacking the Xbox 360 Hypervisor Part 1: System Overview
Diving into the heart of the Xbox 360 security system: the hypervisor. How does it work? Why is it so secure? Find out the answers to these questions and more as I cover the architecture of the Xbox 360 hypervisor and hardware security features that made it nearly impenetrable for 20 years.

- Hacking Microcode of AMD cpusbughunters.google.com Blog: Zen and the Art of Microcode Hacking
This blog post covers the full details of EntrySign, the AMD Zen microcode signature validation vulnerability recently discovered by the Google Security team.

- Reversing Sound Blaster X7 Control for fun and Linux support (2022)sayr.us Reversing Sound Blaster X7 Control for fun and Linux support
My personal setup uses a single DAC to handle Bluetooth, USB and optical inputs. Unfortunately, controlling the DAC through Bluetooth is only supported on mobile. Let’s fix that.
- “Reverse Engineering for Beginners” free book
Direct link
http://ebook.pldworld.com/_eBook/Reverse%20Engineering%20for%20Beginners/beginners.re/RE4B-EN.pdf
Alternative
https://begin.re/
- Assembly Language / Reversing / Malware Analysis / Game Hacking -resourcesgist.github.com A curated list of Assembly Language / Reversing / Malware Analysis / Game Hacking-resources
A curated list of Assembly Language / Reversing / Malware Analysis / Game Hacking-resources - resources.md

Not a fan of game hacking but the list is to useful to be ignored.
- Reverse emulating the NES to give it SUPER POWERS (2022)
YouTube Video
Click to view this content.
- Reverse-engineering the surprisingly advanced ALU of the 8008 (2017)www.righto.com Reverse-engineering the surprisingly advanced ALU of the 8008 microprocessor
A computer's arithmetic-logic unit (ALU) is the heart of the processor, performing arithmetic and logic operations on data. If you've studie...

- Reverse Engineering the Tesla Firmware Update Process (2020)www.pentestpartners.com Reverse Engineering the Tesla Firmware Update Process | Pen Test Partners
TL;DR How does the Tesla Model S update its firmware? What did we find when reverse engineering the display and instrument cluster? Here’s the result of a couple of weeks work, working on a real vehicle that (mostly) worked after we had finished. Part 1: analysing the hardware, complete with a 14 la...
